Hydra is a tool that makes cracking protocols such as ssh, ftp and telnet relatively easy. In my example, I will be cracking SSH using Hyrda 5.9.1 on Ubuntu 10.10 64 bit (. Update for Ubuntu 12.04 - Replace all references of Hydre 5.9.1 with Hyrda 7.3, which can be downloaded ).
Although this example uses Ubuntu, these commands should work on any Debian based system such as Debian and Linux Mint. Hydra uses password lists to brute force the SSH server. If you need help finding a good password list, check here:Here is what my password list looks like (this is a short list that I made solely for this tutorial):To begin, we will need to install a few packages:. sudo apt-get install libssh-dev nmap build-essential linux-headers-$(uname -r) libgtk2.0-dev libssl-dev cmakeI put nmap in there just to do fingerprinting before we attack. Run the following for the nmap scan:. nmap -A -T4 -F 192.168.1.95Use the output to confirm that the SSH server is active.
You also can see what SSH server it is, what protocol, what port, and what operating system it is running.Next, we will download and build Hydra:wget -xvzf hydra-5.9.1-src.tar.gzcd hydra-5.9.1-src./configuremakesudo make installIf Hydra installed successfully, press Alt + F2 to bring up the Run menu. Type “xhydra”, the gui for Hyrda, and press enter.On the Target tab, enter the IP address or hostname of the SSH server, the port, and the Protocol.On the Passwords tab, select the username (yes, you must know the username, unless you want to use a username list), check the “Password List” button, then choose the path to your password list.On the Tuning tab, you can select the number of tasks and the timeout time. I left mine at default, but you may need to edit these if you have trouble with the attack.On the Start tab, click on Start and watch the output.Once it finds a password match (if it finds one), it will be highlighted in black.As you can see, it is quite easy to perform a brute force attack on an SSH server using Hydra. Hydra works with much more than SSH though. You can use Hydra to perform a brute force attack on FTP, Telnet, and POP3 servers, just to name a few. Remember, don't run these attacks on anything other than your own servers.
Again, you should only do this attack on your own servers for testing purposes (to make sure your network is secure). Any server that is in production should have proper security measures in place to prevent an attack such as this. For instance: do not enable root access, setup fail2ban, and have strong passwords.On the other hand, it’s amazing how many people have unpatched ftp servers running on unpatched and outdated operating systems (server 2000 and server 2003 for example).
So for all of you guys who manage systems like these, you should really update your systems and change your password routinely.
Usually, hackers are trying to get into the servers, as these contain juicy, profitable information.Often the servers are more secured than normal computers, as system administrators want to protect the data on these. In today's world, few system admins sit in front of the actual server machines and use a physical terminal.
Instead, servers are remotely controlled via a system called SSH on port 22 ( Secure SHell).However, as any system, it has flaws. In this tutorial we are not going to use a vulnerability, or a bug in the system. Instead, we will use a method which ALWAYS works (given enough time), brute-forcing.I'm going to assume all of you know what brute-forcing is, so I won't go into detail there. However, some may not know what is. THC-Hydra is a password-cracking program, intended to be fast and effective. We will use THC-Hydra to brute-force an SSH password, to gain access to a system. Step 1:The first step, as always, is to boot into your system.
Lazy Ssh 1 7 Crack Download
I'm using Linux Xubuntu, but you can use anything.Open your terminal and let's do some recon! Step 2:Alright, open a terminal and type: /& proxychains &/ nmap -A -p 1-22 (TARGET'S IP)(when I put /& 'command' &/ it means this part is not necessary).
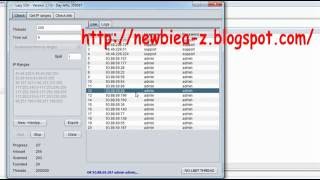
As you can see, nmap returned a lot of information about our target. The part we care about is:22/tcp open sshThis means port 22 or SSH is open! Let's get into cracking.
Step 3:Now that we know that SSH is open on our target, let's crack it. The command for this is: hydra -l (USER TO LOG IN AS) -x 4:10:aA 192.168.8.101 sshBreaking down the command:-l is the user to log in as.-x this is the password generating parameters. 4:10:aA means the password is at minimum 4 characters, and maximum 10, and that it can contain lowercase a-z and uppercase a-z.
1/7 Fraction
Experiment with the options on this one.192.168.8.101 is the IP address of the targetssh is the name of the service we are trying to crack. Step 4:Let her fly! Testing out the command, we can see that THC-Hydra found a working password for the user pi. (i'm hacking a raspberry pi).